In November 2017, a flaw in the code of Ethereum wallet Parity caused $300 million dollars worth in cryptocurrency to disappear in an instant. This was not the work of a hacker, however.
A curious programmer decided to play around with the ownership settings of multi-signature smart contracts and assigned all ownership to himself. In the process of undoing the effects of this test, the programmer deleted the code used to transfer ownership and forever locked up the Ether with no way to access it.
Earlier this year, hackers were able to spirit away more than $30 million worth in Ether due to a security vulnerability again with Parity's system. Just this year, during a so-called "summer of hacks", several cryptocurrency wallets and exchanges encountered security breaches that have resulted in the loss of crypto assets to the tune of millions of dollars in equivalent.
The encrypted, distributed, and immutable nature of blockchains makes it difficult to hack and attack these infrastructures directly. However, vulnerabilities in complementary services make these viable targets for attackers. This is why cryptocurrency exchanges and wallets have become popular targets for hackers, in lieu of the Blockchain itself.
Hackers have already breached several systems and they will continue to do so while vulnerabilities continue to exist. Apart from blockchains and crypto wallets, popular targets will include cloud services and even standalone deployments.
For businesses, this means that whether you run your infrastructure via distributed mechanism like blockchain or through the cloud, or even if you have a simple on-premises deployment, then engaging security services is an essential part of your business.
What then can we do to better protect our data, infrastructure, and digital assets against attackers?
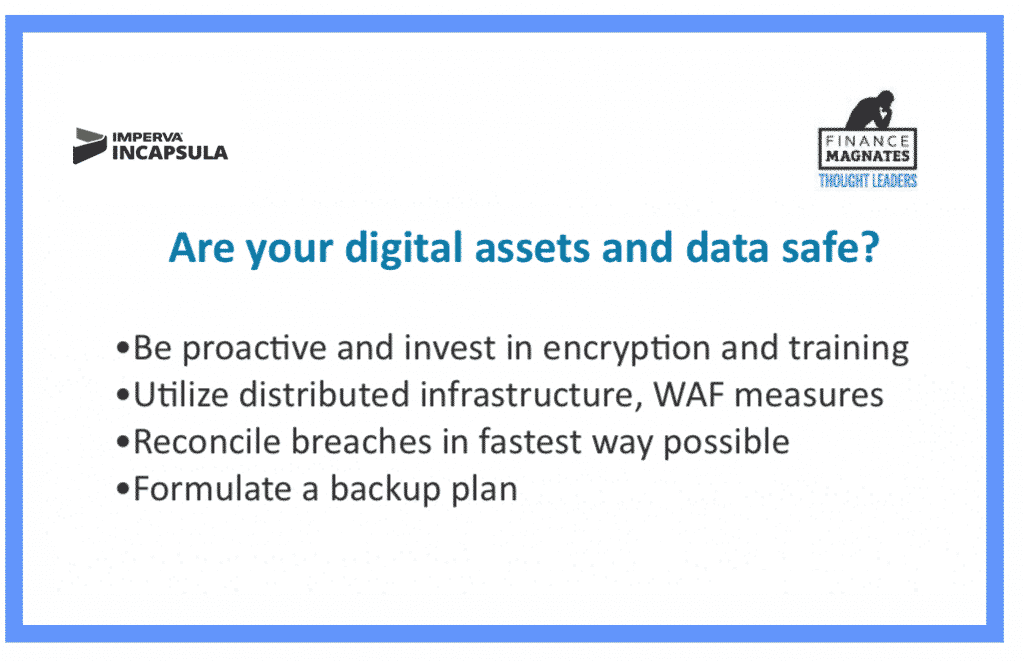
Be proactive
In the Ponemon Institute's 2017 Cost of Data Breach Study: Global Overview done in partnership with IBM, the research analysts points out three strategies in reducing the cost of a data breach. All of these are pro-active approaches to security: engaging an incident response team, extensive use of encryption, and employee training.
This means that the more prepared your business is, the less likely your organization will suffer from an attack. And if you do get attacked, the impact could be greatly mitigated or minimized.
In fact, with an incident response team, the cost per record during a breach is reduced by $19.30. It was reduced by $16.10 with extensive use of encryption, and $12.50 with employee training – out of an average cost per record of $141.
Deploy security measures on a distributed infrastructure
Given the increasing prevalence of distributed infrastructure like cloud and even blockchains, there is likewise a need to focus on distributed security deployments. Incapsula, with its cloud-based web application firewall (WAF), filters out unwanted traffic and blocks web-based attack vectors, which can include cross-site scripting, SQL injections, and similar attacks.
Because the platform runs atop Incapsula's global cloud network, businesses can deploy the service with any type of network infrastructure, be it cloud or on-premises, without the need to install software separately on servers or install physical firewall devices within the network.
A cloud-based WAF can also help mitigate any potential disasters brought about by inherent security vulnerabilities within a web application, which means it can potentially protect your data and assets even when there are unpatched vulnerabilities.
Act for speedy resolution
Data breaches can result in a lot of direct and indirect costs. For example, an organization can be liable to its customers, stakeholders and regulatory agencies whenever data is stolen or leaked. Thus, response speed is critical in reducing the damage and mitigating the detrimental effects of a data breach.
Data from the Ponemon report cites that, on average, it takes 46 days to resolve a cyber attack at a cost of $21,155 per day. Thus, the shorter it takes to resolve it, the less expensive the cost would be for your organization. Of course, being proactive can greatly improve resolution speed, especially when you have engaged a dedicated incident response team.
[Video] Learn why you need a strong #security culture and the four components needed to build one #CyberAware #NCSAM https://t.co/kCGt8aC2Bw
— Imperva Incapsula (@Incapsula_com) November 26, 2017
Establish a backup plan ahead of time
In the event of a hack attack or security breach, one of the first things to go down is your ability to coordinate with your team, with employees, and with customers. This is especially true for organizations that encounter a DDoS attack or when you are taking your infrastructure offline for forensics and to audit the extent of the breach.
When you shut down your internal environment, you need to follow pre-established protocols in communicating with your employees and other stakeholders. It can also be a marketing nightmare – when you require customers to reset their passwords, for example, it could raise a lot of questions regarding the integrity of their data.
You need to plan ahead in order to keep everyone apprised about the situation, so that the effects of the breach do not become worse.
Digital Guardian and the US Federal Trade Commission provide advice on how to handle the customer side of managing the data breach, and this mostly includes open communication both internally and with external clients. This may also mean coordinating with third parties regarding any action that may be needed on their part, such as changing authentication tokens, passwords, and the like.
Conclusion
This is by no means a comprehensive list, although it is definitely good to start with being proactive with your organization's data security and integrity.
Whether you are running a small on-premises business infrastructure, running your platform via the cloud, or you are running a full blockchain node, it pays to keep your digital assets safe and secure. This means thinking about potential risks in advance, addressing these at the outset, and considering backups and failover mechanisms when a breach does occur.
















