Pepperstone CEO Tamas Szabo recently sounded an alarm many brokers quietly share: taking down typosquatted domains has become an almost daily task. Even after securing more than a hundred domain variations, new lookalikes still appear fast enough to occupy an entire fraud team, he said.
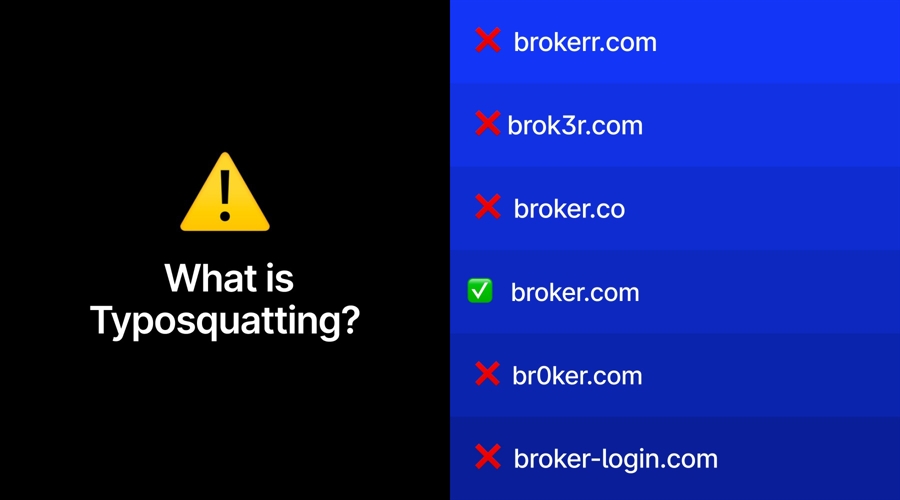
Typosquatting is not a scam in itself, but one of the most common entry points used by scammers – a technical tactic that enables phishing, impersonation and broader fraud schemes.
And this is not an isolated Pepperstone problem – it’s an industry-wide escalation. Brokers across the market report a sharp rise in brand impersonation through lookalike domains, driven by AI-assisted cloning, and the near-zero cost of registering new domains. What used to be an occasional nuisance has become a continuous operational threat.
The scale of the issue is visible in the numbers. “Today, our team identifies new suspicious domains almost every week. Three or four years ago, these cases were sporadic,” said Shawn Young, Chief Analyst at MEXC Research.
Pepperstone reports similar patterns. According to Sarah Rockett, Legal Counsel at the broker, the firm now uncovers one to three typosquatted websites every week, underscoring how persistent and systemic these attacks have become.
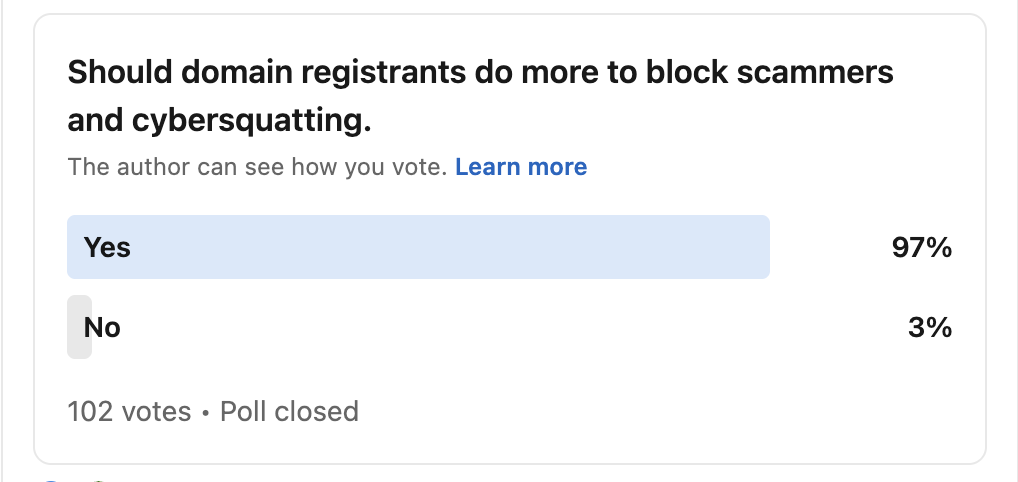
The growing frustration across the industry is also directed at the domain ecosystem itself. In a recent LinkedIn poll shared by Szabo, 97% of 102 respondents said registrars should do more to block cybersquatters – reflecting a sentiment widely echoed in compliance and legal teams.
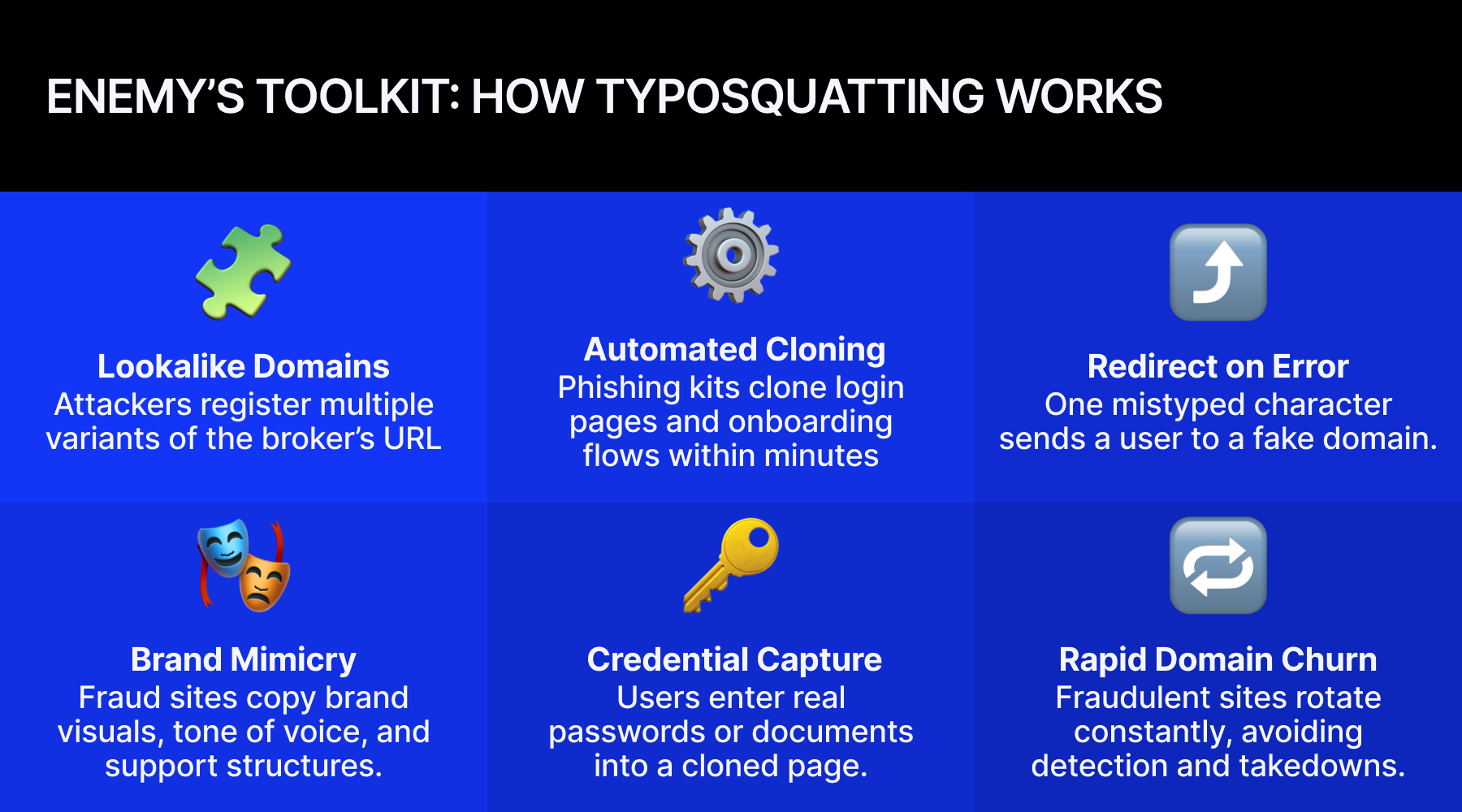
Against this backdrop, the mechanics of typosquatting matter less for their simplicity and more for their scalability. One mistyped letter or deceptive variation is enough to redirect a trader to a cloned login, a fake app, or a phishing funnel built to harvest credentials at industrial speed. That dynamic explains why certain industries, brokers in particular, are disproportionately exposed.
Why Brokers Are the Perfect Target
Typosquatting affects every sector, but not equally. According to IBM research, in 2023, over 20% of all brands impersonated through this technic belong to financial services, second only to IT and far ahead of retail, telecom, or transportation.
This pattern is confirmed by fresh industry data. According to a 2023–2024 report by Akamai, more than 36% of all traffic to typosquatted domains targets financial institutions, making finance the most abused sector online.
This imbalance is not accidental. The structure of the brokerage business puts them at the forefront of this never-ending war. Here are factors that amplify the risk:
Money. Brokers hold exactly what typosquatters want: client funds and account credentials. The financial upside per victim is significantly higher than in most other sectors.
Trust. A broker’s entire value proposition rests on trust, and typosquatters leverage that trust against the broker. No need to persuade anyone to send money to a stranger: they intercept users who are already trying to reach the brand. Traders come pre-sold.
Complexity. The digital-first model brokers rely on also introduces friction and confusion. When users land on a page with a slightly misspelt address, they often see no visible difference from the legitimate site.
New users can hardly distinguish between official onboarding steps and fake ones, making cloned login pages or phishing prompts significantly more effective.
A recent LinkedIn example illustrates how blurred the lines can become: an affiliate openly described running multiple landing pages under lookalike broker domains to capture traffic by building a funnel nearly identical to the real thing. He claims that he has over 40 domains under one broker’s name.
What Are the Consequences for Clients and Brokers?
For clients, the damage is immediate. Many victims genuinely believe they are interacting with their broker until their credentials are stolen or their accounts drained. In most cases, funds are unrecoverable, because they interacted with typosquatters instead of regulated and reputable entities.
For brokers, however, the stakes are even higher. One fraudulent domain can trigger cascading damage across multiple fronts.
The Cost Spiral
Typosquatting generates continuous operational costs. Fraud teams must investigate incidents, escalate takedown requests, work with registrars, review evidence, and communicate with impacted customers. Legal teams are often required for UDRP filings or coordination with law enforcement.
Young describes the workload clearly: “Each case requires anywhere from a few hours to several days of operational effort, depending on the registrar’s response time and the sophistication of the attack.”
Crypto exchanges are, of course, not immune to the risk. Bitget’s security team reports facing these incidents daily, noting that modern impersonation campaigns often expand beyond typosquatted domains to include hijacked social media accounts, fake apps, and spoofed SMS messages.

Trust Erosion
Once a victim interacts with a fake site, the financial and reputational damage is pinned to the real broker, not the scammer — few users will stop to analyse whether a typo in the address bar was to blame. That erosion of trust is far harder to repair than any technical breach.
Pepperstone underscores that reputational harm outweighs all other consequences. According to Rockett, “The reputational damage is the most significant consequence. When the public is defrauded through impersonation sites, they often contact us believing the activity was carried out by us.”
She adds that this not only undermines client trust but also burdens the team with investigations and support for individuals who may have already lost funds.
Revenue Leakage
Stanislav Galandzovskyi, acquisition and growth expert in fintech who worked with brands such as NAGA and Zilch, highlighted a major hidden cost: “Some brokers assume traders will click their organic results anyway. But when typosquatters bid on your brand, your real site may not even appear on the first screen.
This means they can hijack not only organic searches but also paid traffic - diverting advertising budgets into fraudulent funnels and driving up CPC for the real brand.
- HFM Celebrates 15 Years of Empowering Traders Through Education and Trust
- Vantage Gears Up for iFX EXPO Dubai 2025: Innovation, Insights, and Empowerment in Trading
- Fixed-Fee Subscription Model Eliminates Brokers’ Revenue Risks, but Is It Sustainable?
Beyond lost traffic, typosquatting incidents trigger broad internal disruption. Fraud, compliance, marketing, support, legal and IT security teams are often pulled into emergency response, halting projects and stretching resources across the organisation.
Regulatory Friction
Even when brokers are the victims, typosquatting incidents often trigger additional scrutiny. Firms must demonstrate that they took “reasonable steps” to protect clients producing documentation, internal procedures, and evidence of proactive brand protection.
At the same time, regulatory tools remain largely reactive by design. Warnings and blacklists usually appear only after investors have already been targeted.
CySEC Chair Dr. George Theocharides has acknowledged this limitation openly: “No matter what regulators do, there will always be someone who finds new ways to deceive investors.”
This creates a structural gap: brokers are expected to prevent damage in real time, while enforcement mechanisms inevitably lag behind fast-moving typosquatting campaigns.

What to Do? A Survival Guide for Brokers and Traders
Typosquatting isn’t something a broker can eliminate entirely, but it can be managed. Effective protection requires a combination of proactive controls, monitoring, legal readiness, and clear communication.
Proactive domain registration
Registrations of common misspellings and alternative extensions reduce easily exploitable opportunities. According to Galandzovskyi, this is one of the tools available for brokers. He mentioned one company that bought over 600 domains to reduce impersonation risks - a costly but effective measure.
Branded search campaigns also act as a defensive layer, keeping the official site above fraudulent ads - a small cost compared to the impact of impersonation.

Continuous Monitoring and Fast Takedowns
Pepperstone’s legal team notes that the main bottleneck often comes not from registrar responsiveness but from the legal thresholds embedded in the domain ecosystem. The firm now outsources takedowns to a third-party provider simply because of volume.
“Registrars are generally responsive, but they aren’t required to take action without a court order or a UDRP complaint,” said Rockett, “This is why we go to hosting providers first.”
While many hosting providers cooperate, Rockett notes that some ignore takedown requests or operate in jurisdictions without DMCA (Digital Millennium Copyright Act)-style laws, forcing brokers into slow and costly UDRP (Uniform Domain-Name Dispute-Resolution Policy) proceedings.
Modern tools help by tracking new domain registrations and detecting lookalikes early, but Pepperstone stresses that human reporting remains essential: employees and clients still identify a large share of fraudulent sites.
Early Detection Signals and the Limits of External Alerts
Technology alone is not enough. Marketing teams increasingly act as an early-warning layer. As Galandzovskyi notes, search-monitoring platforms often reveal impersonation attempts before domains even go live: “If CPC suddenly spikes and CTR drops, it may signal someone is bidding on your brand - often attackers.”
He argues that the biggest mistake is reacting only after an incident has already begun, rather than monitoring brand mentions and cloned pages continuously. Regulators help but are inherently reactive.
They publish alerts on clone firms almost daily, yet these lists appear only after users have already been targeted, which is why brokers cannot rely on regulatory notices alone and must maintain real-time internal monitoring.
Client communication and education
Both MEXC and Bitget stress that proactive client education - highlighting common phishing patterns, pointing customers to verified channels, and reinforcing safe login habits - significantly reduces successful attacks.
Many firms now maintain verification hubs where users can check domains, emails, or social accounts, and some implement anti-phishing codes in every official email.
Ignoring negative reviews or scam complaints is risky: both app stores and clients may interpret silence as acknowledgment or even complicity. Consistent, transparent communication remains one of the strongest defences brokers can deploy.