Over the weekend, $10 million was stolen through an exploit on the Rari Capital decentralized financial protocol. A hacker manipulated a smart contract to withdraw large amounts of ETH tokens, draining the protocol’s supply. While Rari has already formed a plan to compensate affected users, the exploit is only the latest in a series of multi-million dollar thefts from decentralized finance platforms.
For example, earlier this year, EasyFi lost as much as $60 million through a vulnerability in its software; also ForceDAO lost $367,000 in early April.
Martin Gaspar, Research Analyst at CrossTower, told Finance Magnates that: “According to The Block, approximately $120 million of funds were stolen in DeFi hacks in 2020.” However, “This has already been exceeded in 2021, with approximately $300 million of exploits so far,” he said, citing the list of exploits maintained by DeFi media platform Rekt.
In addition to hacks and exploits, the DeFi ecosystem has been targeted by regulators as a possible breeding ground for money laundering and other financial crimes. Fake DeFi platforms have appeared and then quickly disappeared in a growing number of 'rug pull' scams.

Martin Gaspar, Research Analyst at CrossTower.
What is causing the rise in DeFi-related cybercrime?
As DeFi Grows, Hackers and Criminals Are Following the Money
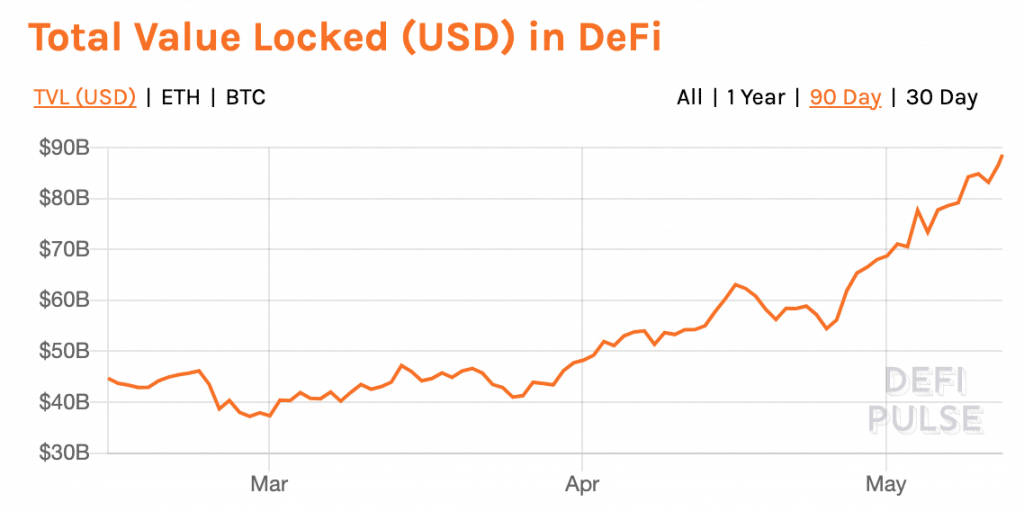
One of the main drivers, if not the main driver, of the growth of crime in the DeFi sector is the simple fact that DeFi is growing larger and larger. Gaspar stated that: “higher total value locked (TVL), or deposits, across DeFi protocols in 2021, may be further incentivizing attackers.”
Indeed, on January 1st, 2021, there was $15.1 billion 'locked' into DeFi protocols. At press time (just over five months later), that figure had ballooned to more than $88.6 billion.
As DeFi has grown, hackers have followed the money. Monica Eaton-Cardone, Co-Founder and Chief Operating Officer of Chargebacks911, told Finance Magnates that without intervention, this trend could continue unabated: “If prices start to climb, we'll see a major migration to DeFi platforms,” she said.
Parallel phenomena can be observed with the growth of the cryptocurrency industry in general. As market caps got higher, crime got bigger. Additionally, “Last year, when the COVID lockdowns forced millions of consumers to rely on eCommerce and home deliveries for the first time, there was a big rise in cybercrimes,” Eaton-Cardone pointed out. “Online shoppers were defrauded because they didn't really understand how the digital world worked.”
Similarly, as more new users continue to enter the DeFi space, they could become a larger target for malicious actors. “Bluntly stated, inexperienced consumers make mistakes and are more vulnerable to fraudsters and thieves,” Eaton-Cardone said. “If millions of inexperienced investors migrate to DeFi platforms, the cybercriminals will certainly be waiting.”
“Crypto-hackers are already stealing billions annually; trust me, they're salivating at the prospects of a rapid influx of new, inexperienced targets. Defi isn't exactly easy for everyone to use. There are complexities that can–and most certainly will–lead to costly mistakes.”

Monica Eaton-Cardone, Co-Founder & COO of Chargebacks 911.
Staying Safe in the DeFi World
In addition to new users, the proliferation of DeFi platforms has led to the creation of many new DeFi platforms. As such, some analysts have compared the DeFi boom to the ICO bubble of 2017 when many new projects were created and abandoned as cash grabs.
While the situation is not entirely the same, the fact remains that not all DeFi platforms are created equal. As such, some may be much more vulnerable to attack than others. Fintech consultant Gaurav Sharma, who is the founder of BankersByDay.com, told Finance Magnates that some platforms may have “scrambled to upscale their online operations and didn’t have enough time to secure and loopholes.”
As such, Gaspar said that: “The most common crime seems to be exploits in which an attacker uses a function in the code in a way that its developers and auditors overlooked.”
“This typically allows them to swap assets in pools for a greater amount than was intended to be possible, or to simply withdraw funds from a protocol,” he said.
Therefore, there is still a large amount of 'buyer beware' in the DeFi space, users have to go above and beyond the surface to stay safe in the decentralized finance ecosystem: “A good approach to staying safe is to only use DeFi protocols that have several audits and that have not experienced an exploit for at least several months,” Gaspar said.
“That being said, there is always a risk that even the most tried and tested protocols could be exploited somehow.”
“The Big Unsolved Problem Is What Evolving Regulatory Requirements Will Mean.”
And certainly, while there are DeFi platforms that may have unintentionally (or intentionally) been left vulnerable to exploit, internal industry safety standards are slowly developing for DeFi.
Doug Schwenk, the Chairman of Digital Asset Research (DAR), told Finance Magnates that: “Certainly the sophistication in design and build [of DeFi protocols] are improving.”
Therefore, “The big unsolved problem is what evolving regulatory requirements will mean,” he continued.
“FATF has recently released a consultation for comment that could imply decentralized exchanges, and other DeFi systems would need to implement traditional financial institution compliance, such as KYC and AML,” he explained, adding that: ”Those changes would require a fairly significant new approach by DeFi platforms if they come to pass.”
Indeed, they would. At the moment, one of the selling points of most DeFi platforms is that they can be used completely anonymously. On the one hand, this removes barriers to entry for people who may not have the means to identify themselves according to traditional financial industry standards. On the other hand, this may allow money laundering and other kinds of financial crime to go unchecked.

Doug Schwenk, Chairman and Chief Executive of Digital Assets Research (DAR).
"Defi platforms are attractive, at least in part, because they bypass certain banking regs,” Eaton-Cardone told Finance Magnates. “Anyone with a smartphone can lend or borrow. Customer verification isn't as strict. So, by their very nature, DeFi platforms are going to be more vulnerable."
"It's a tricky balancing act because we covet the financial freedoms that come with being unregulated, but at the same time, consumers expect the protections that can only come with regulations.”
As such, Schwenk said that: “The greatest concern by regulators may be money laundering, which is difficult to prove or disprove with the readily available data, though some firms are tackling it.”
And indeed, a wave of regulation could be headed straight for DeFi. Gaspar told Finance Magnates that: “Law enforcement has been investing in Blockchain Analytics solutions that can track user activity on public blockchains.”
“In addition, The Financial Action Task Force (FATF) has suggested in recent guidance that virtual asset service providers (VASPs), which may include DeFi protocols, could need to collect information on the users that interact with them.”
When the Nature of the Cyberthreat Changes, the Platform Must Change with It
The bottom line is this: as DeFi grows, the amount of crime will also grow. Therefore, the amount of regulation will continue to grow in an attempt to keep regulations in check.
"Cybersecurity is an eternal, never-ending game of cat and mouse, with both sides constantly striving to one-up the other,” Eaton-Cardone stated. “But in today's game, both sides are trying to build the better mousetrap. Both sides are investing in R&D. It's become a hi-tech arms race, with the good guys using technology to build and protect, and the bad guys using technology to infiltrate and reverse-engineer. “
"Nobody knows for sure what the various financial platforms will look like in 10 years, but I guarantee you, they'll look strikingly different than they do today because the cyberthieves will have rendered our current platforms obsolete,” she continued. Codes can be stolen, compromised and cracked. Unfortunately, time is on the side of the criminals.
"When the nature of the cyberthreat changes, the platform must change with it, or perish because of it."






















