More than $4 billion was stolen in 255 crypto hacks in 2025, according to Global Ledger. The data reveals a major shift: criminals now use slower laundering techniques, posing new, ongoing risks for financial institutions.
Hackers now rapidly move funds at the moment of attack, but intentionally delay laundering—spreading it over days or even weeks. This creates delayed exposure, complicating detection and risk management for brokers and exchanges. The findings come after another year of elevated crypto crime.
Chainalysis data showed that funds stolen through hacks surged in 2024 compared to prior years, marking the fourth consecutive year in which annual losses exceeded $1 billion.
New Laundering Pattern
The 2025 report from Global Ledger analyses the full lifecycle of stolen funds and highlights what it describes as a two-speed playbook.
Hackers often move funds within 2 seconds of an exploit, with 76% of transfers occurring before public disclosure, reducing the window for intervention.
However, the subsequent laundering slows, with attackers employing multi-stage techniques such as cross-chain bridges and privacy tools. It now takes an average of over 9 days to reach the cash-out point.
- North Korea-linked Hackers Stole Over $2B in Crypto So Far in 2025: Report
- Crypto Fraud Losses Fall, But Hacking Sees a 17% Jump in 2024
- Crypto Hack Losses Fall in December, but 2024 Ends Up 40%
The $2 Billion “Sleeper” Exposure
Nearly $2 billion in stolen 2025 funds remains parked in attacker-linked wallets. This creates a sleeper threat as illicit assets may reenter regulated venues later, heightening compliance challenges.
For brokers and exchanges, point-in-time address screening may miss emerging threats. Illicit funds might resurface long after the original attack, evading detection by static systems.
The Changing Toolkit
The report also notes shifts in laundering infrastructure as over $2.01 billion in stolen funds were routed through bridges, fragmenting transaction trails.
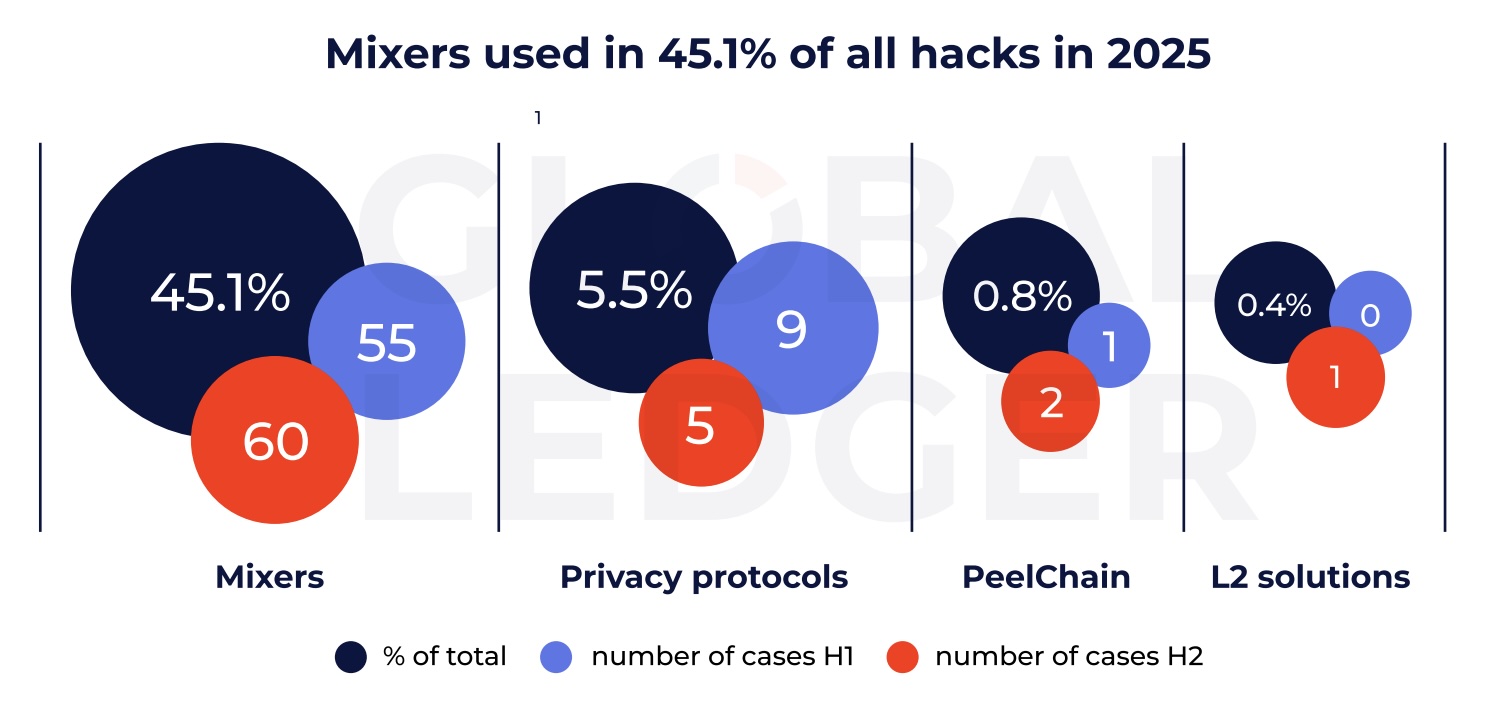
Meanwhile, Tornado Cash saw renewed usage following the lifting of sanctions in March 2025. In the second half of the year, the mixer was used in nearly 75% of hacks involving mixers.
For compliance teams, operational risks are intensifying. Longer laundering timelines and complex pathways demand more robust, continuous monitoring—outdated blacklists are no longer sufficient.